Table of Contains
- Introduction
- 1.The Principal Concepts
- 2.Approach to Document Handling
- 3.Document and Information System
- 4.Future Document and Information Management
- 5.Document Categories Covered
- 6.Document and Information Control
- 7.Implementation of Document and Information Management
Introduction
Objective of this Webpage
This page aims to provide an easy-to-understand explanation for beginners on how to manage the operational aspects of document circulation, sharing, and storage.
It primarily targets those promoting organizational digitization and those considering systematic and organized handling of electronic documents.Following an overview of the digital society and the current state of documents, Chapter 1 introduces key concepts related to document information management. Chapter 2 outlines approaches to document handling, Chapter 3 provides an overview of document information systems, and Chapter 4 discusses future directions for document information management. The subsequent detailed sections outline: Chapter 5 covers target documents; Chapter 6 addresses controls such as creation standards, retention periods, classification systems, and access rights management; and Chapter 7 provides an overview of document information management operations.
From Document Preservation to Distribution/Circulation and Sharing
The amended Digital Procedures (Digital First) Act and the Basic Act on the Formation of a Digital Society came into effect in 2021, marking the start of a full-scale transition to a digital society involving both public and private sectors.
In the e-Document Law, the 2021 amendment also abolished measures allowing the preservation of printed documents to substitute for the preservation of electromagnetic records related to transaction information.
Already, nearly 100% of business documents are created electronically. With the spread of the internet, documents are distributed and shared electronically. Furthermore, organizations are not only utilizing the rapidly increasing volume of electronic documents and data but also beginning to accumulate knowledge and generate added value through AI-driven reproduction.
To ride this wave, mechanisms for systematically and organizationally handling and managing electronic documents as assets are essential.
1.The Principal Concepts
1.1 Document
In describing the principal concepts of the document, the 1901 judicial precedent of the Supreme Court of Judicature of Japan is quoted frequently. This precedent led to the establishment of the following three characteristics as the requirements that constitute a document.
(1)Information is written in characters and symbols that serve as their substitute.
(2)Information is written on some physical object and is in a permanent state.
(3)Information expresses intent.
Today, photo images and computer data are now included in (1) along with characters and symbols.
Additionally, the physical objects on which information is written and described in (2) may be paper for a paper-based document and electronic media for an electronic document (referred to as electronically stored information or ESI). In the case of an electronic document is not to be merely written on electronic media but must be available for reading and comprehension by means of display via a monitor screen or printout.
Document ranges widely in format, such as printed matter, structured data, unstructured data, scanned paper and facsimile sheets, e-mail, audio, video, animation and webpages that include images.
Recently, to facilitate automated processing, documents are evolving beyond human readability alone. Examples include adding tags to Word documents to indicate sentence structure or embedding XML data within PDF documents, transforming them into formats processable by computers.
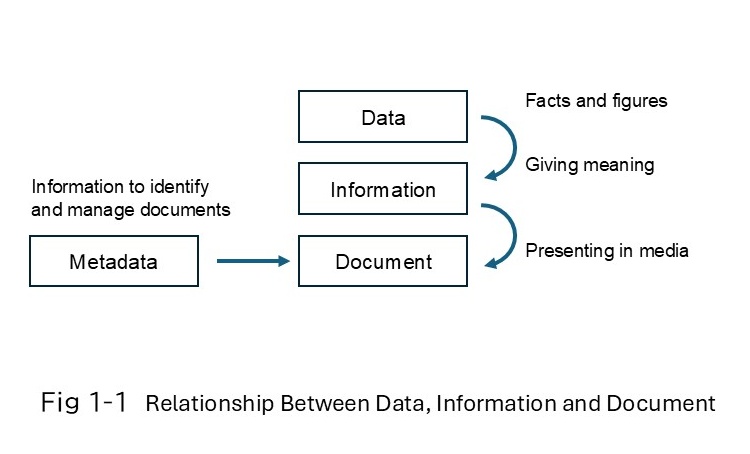
1.2 Document and Information
The Japan Image and Information Management Association (hereinafter called JIIMA) define "document and information" as documents handled in business and information for identifying and managing those documents. The definition not only includes conventional documents, drawings, vouchers and reference materials but tabular data and images as well.
1.3 Document and Information System
Document The Japan Image and Information Management Association (JIIMA) define “document and information” as “documents handled in business and information for identifying and managing those documents.” This “information for identifying and managing documents” encompasses various types and names, including file reference tables, background information, logs, and metadata as a general term.
In the transitional phase of rapid business digitization, electronic documents are now being stored and scattered in various business systems and services, including electronic contracts, electronic billing statement issuance, electronic payment and settlement, and accounting and employee attendance management, making Document and Information Management extremely important in the control and management of such data.
1.4 Document and Information Management
Document and information management refers to the " the systematic handling of document and information under an information governance policy" Its objectives are greater business efficiency, information and knowledge sharing and the reduction of document volume, as well as the assurance of accountability, compliance with laws, action in legal proceedings, internal controls, business continuity planning (BCP), information security, risk management and the assurance of rights (assurance of intellectual property rights and right of prior use).
The term "management" does not suggest supervision or control in accordance with rules. Rather, it refers to the "skillful handling and processing of people, materials and events" as in quality management and environmental management. Document and Information Management should be understood as planning, implementation and administration for the efficient and effective handling of documents by each organization.
2. Approach to Document Handling
2.1 Required Characteristics of Documents
Documents are important information assets for a business enterprise. In conducting business or administrative operations, data transmission and sharing and the reporting and recording of results are essential. Additionally, its effective utilization as knowledge is vital in efficient business management.
Although document requirements differ slightly by varying laws and guidelines, they are generally required to comprise the following characteristics.
a) Authenticity
This characteristic demonstrates that the content was created by the author themselves, based on their intent, at the time and date claimed. Ensuring authenticity is effectively achieved through digital signatures, timestamping, access controls, and recording of operation histories.
b) Integrity
This characteristic demonstrates that the document is properly controlled, complete, and has not been altered. It must be protected from unauthorized modification or deletion (tampering or destruction). If revisions are necessary during the retention period, a record of those revisions must be obtained. Effective methods for ensuring integrity include managing document hash values, implementing access restrictions, and recording change histories.
c) Reliability
This characteristic indicates that the content is reliable as a sufficient and accurate representation of processes, activities, or facts. Effective methods for ensuring reliability include standardizing document handling procedures, verification by responsible parties or content review, validation based on trustworthy sources, and confirming consistency between related documents.
d) Readability
This characteristic indicates that documents and data are readable by humans or machines. When referring to humans, it is also called legibility. Electronic documents cannot be handled by people unless they can be displayed on a screen or printed on a printer for reading. Ensuring readability is effective through format standardization and preparing for equipment deterioration and technological obsolescence.
e) Usability
This characteristic indicates that a document can be searched, referenced, and its content understood. It is particularly important during the preservation period. Ensuring usability is effectively achieved by adding searchable metadata, evaluating and improving usability, and implementing appropriate migration during long-term preservation.
2.2 Legal admissibility of evidence
In terms of legal admissibility of evidence and permissiveness (approval given for preservation or submissions in non-paper formats) of electronic document, the conditions basically remain the same as those for paper-based documents, so long as the requirements above are satisfied.
It is believed that there is no actual benefit in determining whether an electronically produced document is the original or otherwise when there are multiple copies of the same information.
Depending on the organization, document may be managed in a way to differentiate the original from the copies, due to statutory or administrative needs.
2.3 Layering Electronic Document Handling
To manage electronic documents electronically, operations are layered into parts specific to individual tasks (e.g., quote requests, orders, invoices) and parts common to all tasks (e.g., document distribution/circulation, receipt, sharing, storage). The common parts are controlled to meet the required characteristics of the documents.
By generalizing these common business functions, they can be provided as services. Various cloud services have already emerged, such as those for issuing and storing invoices, or distributing documents as alternatives to email attachments.

2.4 Document Handling Phase and Document Preservation Phase
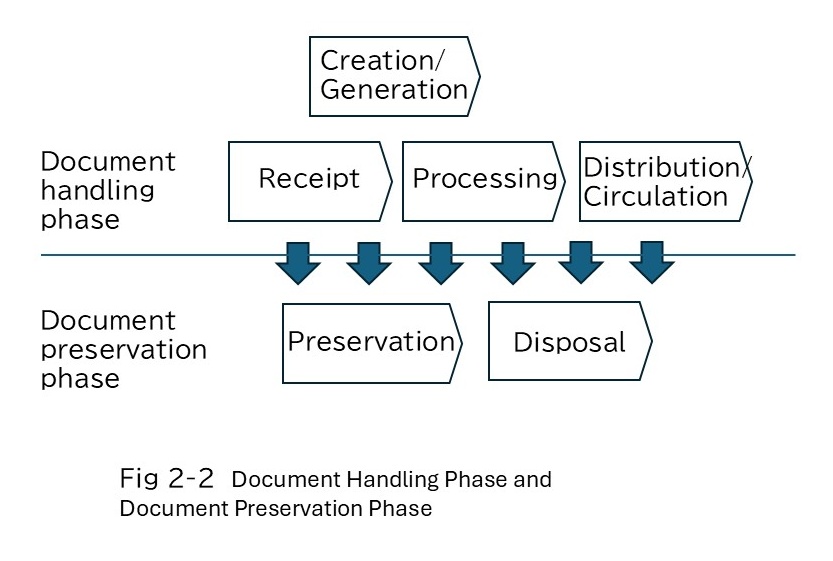
Traditionally, the “series of processes from document creation, acquisition, processing, and storage to disposal” was referred to as the document lifecycle.
However, as electronic documents became central and documents are now routinely saved as evidence of processes, processes in the document handling phase and the document preservation phase are increasingly conducted in parallel, as shown in Figure 2-2.
Note: In document and information management, the term “handling” may be distinguished between its general meaning and the controlled “handling” within the document handling process.
2.5 Recording and Preservation of Contextual information
Preservation of document now covers not only the content (the substance of the document but also the recording and preservation of the background that led to its creation, the procedure up to document approval and time-series data regarding sending, acquisition, etc. Such data is collectively called context data, while the substance is called content data.
Figure 2-3 shows the relationship between content and context. In this illustration, the types of document that is created or acquired are, for example, billing statements and receipts.
3. Document and Information System
The document and information system is integrated into dedicated systems such as enterprise document management (EDM) and enterprise contents management (ECM) systems as a built-in function and is available in appearance as a business system.
The functions of the document and information system are generally the following.
- Classification and ID assignment
- Preservation and disposition
- Search and viewing
- Editing, revision (version management) and reduction
- Authority setting and access control
- Workflow coordination (approval coordination, etc.)
- Monitoring, reporting and audit
In reality, various business systems and services are interconnected in many cases, prompting the need of coordination with a dedicated document management system and customization in order to align the functions and interface as a document and information system. However, such alignment is not necessarily possible due to technical reasons and cost.
Vital in doing so is to have an accurate assessment of the differences and what is deficient or excessive, introduce ideas in system and service configurations and/or add manual work to fill any needs in the business operation procedure.
Substitution with a file server
Japan falls behind Western nations in the implementation of document and information systems. Instead, many organizations appear to make use of file servers as substitute systems.
Even if documents are created or acquired electronically, if they cannot be controlled electronically, business processes cannot be completed digitally. There are limits to covering this operationally through manual intervention.
4. Futere Document and Information Management
4.1 Challenges and Direction for Solutions Document and Information Management of the Future
Until now, document and information management involved dealing with the phase of transition from paper-based documents to document information centered on electronic formats. It was in fact the replacement of paper documents with digital documents, while business operations have basically remained unchanged.
The next step is expected to be the resolution of the following issues regarding the digitization of business operations and implementation of business activities completely in digital formats.
A structure that is versatile enough to adapt to advances in digitization that are underway,
The assurance of credibility of the document received via non-physical interaction.
Action on AI/robotic process automation (RPA).
Note: The credibility mentioned in (2) does not refer to the reliability of the equipment used. Rather, it points to the credibility of the document content, in that its processing, activities and evidence are sufficient and accurate in expression.
A structure that is versatile enough to adapt to advances in progress in digitization.
As mentioned earlier, electronic contracts, e-billing, electronic settlement of accounts, accounting, employee work attendance control and many other services are today cloud-based, with document information storage being dispersed among various cloud services. These services are expected to continue evolving and changing at a speed exceeding business reforms.
For this reason, document to be handled must be structured in such a way that it can withstand such changes and developments.
The method regarded as an example of good practices in terms of resistance to change involves the creation of a flat organizational structure and segmentation of its business operations into units that can exercise the maximum amount of autonomy possible. This was roughly 200 units in the overseas cases studied, although this would be dependent on the line of business and organizational scale. The business workflows are identified clearly, with document created or acquired in the operation linked to the business operation and the organization, and the systems and applicable services linked to the operation.
Also, it must be noted that the definition of the business operation and workflow are basic to internal control.
This structure enables what documentn is being used where. Even when a part of the operation is replaced by another service, the impact of document and information management in other operations can be minimized.
The assurance of the credibility of document received via non-physical interaction.
Business transactions in cyberspace are non-physical, conducted without any actual encounter with the other party. The credibility of the other party in the transaction and of the document received is a major issue.
A transaction via the web involves a variety of risks, such as identity theft, non-delivery, discrepancy in format and failure to determine the reliability of the document content.
Since the reliability of the transaction partner and document information received depends on factors such as the use of a trusted service provider (with an e-seal verifying that the document is issued by the organization in question), previous communications, contracts and trade transaction records, the quality of the mediating service provider and acquisition of third-party authentication, etc., the selection of a suitable verification method is expected to become possible with systematization of the requirements and disclosure of the level of trustworthiness.
Action on AI/robotic process automation (RPA).
Presently, data input involves either printing out hard copies or displaying the data on a monitor screen and transcribing the data into a ledger (e.g., database or Excel table). Automation is not possible if the data is not machine-readable but is human-readable only.
If data can be extracted mechanically from the acquired document, it can be written into a database and the processing completed instantaneously, preventing transcription errors.
For AI use in the mechanical extraction of data from acquired document, actions such as following must be executed.
Tags are added to the content to indicate where the data is embedded.
The document is made readable to both humans and machines via the use of XML, for example.
Machine-readable table data is attached to human-readable body text (such as embedding XML data in a PDF). In such a case, an explanation must be given to prove that there is no discrepancy between the body text and the table data.
It must be noted that AI-OCR is now available to enable the mechanical extraction of data from document received in paper form.
4.2 Relationship with Records Management
Document and Information Management covers the handling process (creation, acquisition, etc.) and the retention process (storage, disposal, etc.) of documents. However, the process of preserving documents as records incorporates part of Records Management, as shown in Figure 4-1.
The concept of Records Management has been thoroughly discussed in ISO and other bodies and is standardized as JIS X 0902-1.

5. Document Categories Covered
The categories of document covered in document and information management are the following.
- Documents required to be preserved by law
- Management system documents
- Documents pertaining to trade secrets
- Documents for verifying accountability
- Documents for self-defense
5.1 Documents Required to be Preserved by Law
Document that is required to be preserved has varying designated preservation periods.
As shown in Table 5-1, there is a wide range of documents that are required to be preserved by law, in addition to documents pertaining to each organization that must be preserved due to the different laws that regulate document management in each industrial sector.
Moreover, careful attention must be directed toward the possibility of new additions to documents to be preserved, as a result of amends to laws, etc.
Table 5-1 Examples of Documents Required to be Preserved by Law
| Business Category | Type of document | Name of Law |
|---|---|---|
| Accounting | Books and documents pertaining to transactions (price quotations, delivery statements, billing statements, contracts, receipts, etc.) | Article 126-(1) Corporation Tax Act |
| Personnel Affairs | Important documents pertaining to labor affairs; e.g., recruitment, dismissal, accident compensation and wages (work attendance ledger, payroll ledger, etc.) | Article 109 Labor Standards Act |
| General Affairs | Copies of the minutes of general shareholders meetings and general assembly meetings | Article 318-(2) and 318-(3), Companies Act |
In addition to the above, there are guidelines and ordinances that have been announced by the Japanese government, etc., that must be complied with while executing various business operations. These guidelines specify the documents that require preservation and the methods for creating and preserving documents designated for mandatory preservation.
5.2 Management System Documents
Management systems established in compliance with ISO 9001 (JIS Q 9001: Quality Management Systems) and others have been adopted by numerous business enterprises, in recognition of its effects in boosting social credibility by acquiring certification under such systems.
Under these management systems, documentation of the management organization, management activities, etc., and preservation of the documented information are mandatory.
5.3 Documents Pertaining to Trade Secrets
Leakage of confidential information requires careful controls, since it may lead to the decline of the business enterprise's competitiveness, erosion of its social reputation as a result of violation of the law or contracts with its business partners, and damage of the relationship of trust with other companies.
Examples of trade secrets are shown in Table 5-2.
Table 5-2 Types of Trade Secrets
| Information Asset Category | Leading Example of Information in the Category |
|---|---|
| Information Assets Related to Management Strategies | Management plan, targets, strategies, new business plans, merger and acquisition plans, etc. |
| Information Assets Related to Customers | Personal information of customers, customer needs, etc. |
| Information Assets Related to Sales and Marketing | Information on sales collaboration partners, sales target information, sales & marketing know-how, purchase price information, supplier information, etc. |
| Information Assets Related to Technology (Including Manufacturing) | Joint research information, information on researchers, materials information, diagrams information, manufacturing technology information, technical know-how, etc. |
| Information Assets Related to Business Administration (Personal Affairs, Accounting, etc.) | Internal system information (IDs & passwords), system configuration information, security information, personal information on employees, personnel evaluation data, etc. |
| Other Information Assets | Information assets other than the above |
Management Guidelines for Trade Secrets: Procedures for Trade Secret Management, Ministry of Economy, Trade and Industry, Aug 2013.
5.4 Documents for Verifying Accountability
Documents that prove that internal controls are functioning and the organization is being managed properly are preserved to verify accountability.
Business enterprises are granted discretion in determining the scope of documents for and pertaining to internal controls and the preservation period for such documents. However, the period is generally set at five years for these documents and applies to related substantiating documents as well.
5.5 Documents for Self-Defense
This type of document does not require preservation by law and is not used under ordinary circumstances. It is preserved to serve as substantiating evidence in case of litigation, to prepare for disasters and other actions in case of any other exigency.
1) Documents pertaining to product liability
The Product Liability Act requires that manufacturers, etc., bear the responsibility for compensation if the life, body or property of others is harmed due to a defect in a delivered product (movable property) that had been manufactured, processed, imported or by a manufacturer, etc., or on which there is a specific indication, regardless of whether the manufacturer, etc., is at fault. Records pertaining to manufacturing processing, shipment and sales of the product, as well as quality control data, must be preserved until the preservation expiry date.
2) Vital records
Information essential for the continuity and survival of the organization when facing an emergency is collectively called vital records. A business continuity plan (BCP) is also related. However, essential information may vary by the type of business and hence requires an independent risk analysis by the business enterprise.
Regular review is important because of the changes that take place in vital records with changes in the line of business and within the business environment.
Additionally, vital records must be stored in an accessible location not only in electronic format but also as hard copies, in view of the possibility that computers may become unusable in an emergency.
Note: For further details, see JIIMA Record and Document Management Guidelines for Crisis Control.
3) Documents pertaining to the preservation of skills, knowledge of retirees and knowledge management
To preserve and carry on the manufacturing skills of veteran technical workers that had been depended on due to their personal expertise and intuition, it is urgently necessary to convert tacit knowledge (intuitive knowledge, personal insight and experience-based know-how) to format knowledge (objective and rational knowledge that can be expressed with words or body of text, numerical equations, diagrams, photos, videos, etc.) and preserve it as records.
4) Documents related to patents
In some cases, trade secrets (see 5.3) are kept confidential as know-how rather than disclosing it for patent application. Although this may keep production methods, etc., away from the eyes of competitors, there is the possibility of a competitor developing technology independently and filing for patent(s) on the technology. Even after a patent application by a competitor, the right of prior use (under Article 79 of the Patent Act) can be claimed, so long as the business making use of the invention has either started up or preparations are underway to do so. To substantiate this, technology-related documents (research notes, technological results reports, design diagrams and product specifications), business-related documents (business plans, documents certifying business startup decisions, estimates, delivery invoices, work logs at the manufacturing plant and product catalogues) and others must be preserved as evidence.
6. Document and Information Control
The following controls make possible the unified implementation of document and information management.
6.1 Document Creation Standards
Policy and standards are established in advance regarding which documents are to be created or acquired and how long they are to be preserved.
The process of evaluating business standards according to these standards is called appraisal. In addition to gaining an understanding of the nature of the business operations, statutory requirements, the state of resource preparation and the technological environment, the decision is made on which documents are to be created (or destroyed) and how they are to be managed, in response to the risk assessment results.
An appraisal is to be conducted in the following cases.
- At the startup of a new organization.
- Upon the loss or acquisition of a business operation or activity.
- With any change in business methods or needs, change in the regulatory environment, introduction of a new system or a system upgrade.
- Upon any change in awareness toward risks and priorities.
6.2 Retention Period
In face of the steadily growing volume of document, data that is no longer heavily used and/or left untouched not only builds up dormant physical resources but also raises the risks caused by long-term, wasteful storage. For this reason, it is necessary to define an appropriate preservation period and dispose of unnecessary data at regular intervals. Standards on preservation are needed to prevent document from accumulating, but at the same time prevent the disposal of data that is necessary.
Generally, the preservation period for documents and document in business enterprises and government organizations is set forth by law and the document management regulations by each business enterprise. The schedule for document presentation and disposal is managed in compliance with the regulations (called retention management).
Retention begins when a document enters the retention process. The “retention period commencement date” marks the start, and the “retention period expiration date” is reached once the specified “retention period” has elapsed.
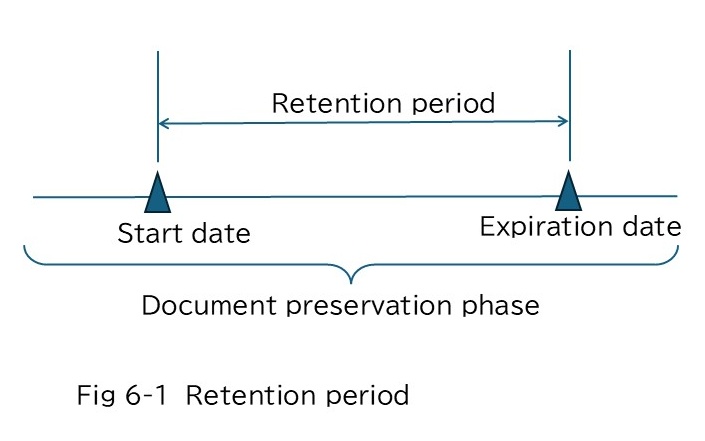
Examples of the retention periods for statutory preservation documents are shown in Table 6-1.
Table 6-1 Examples of Document Retention Periods Designated by Law
| Type of Document | Preservation Period | Law |
|---|---|---|
| General shareholders meeting minutes and commercial ledgers | 10 years | Companies Act |
| Ledgers such as daybooks and general ledgers, inventory control charts, balance sheets, profit and loss statements, purchase order sheets, quotation sheets and copies of contracts | 7 years | Income Tax Act and Corporation Tax Act |
| Application forms for asset-formation tax-exempt savings programs and application forms for exemptions | 5 years | Income Tax Act |
| Documents pertaining to persons insured by unemployment insurance | 4 years | Employment Insurance Act |
| Workers’ register and documents pertaining to recruitment, discharge and retirement | 3 years | Labor Standards Act |
| Notices confirming eligibility of persons insured by health insurance | 2 years | Health Insurance Act |
Note: Although ledger-related documents are required to be preserved for seven years under the Corporation Tax Act, the period has been extended to 10 years under the tax scheme amendment of 2016 for documents for the fiscal term during which the retained losses are reported.
Regarding documents for which the preservation period is not stipulated by law, the period must be decided voluntarily by the organization under its own business regulations.
6.3 Classification scheme
There are two main classification scheme related to document information management.
(1) Business Classification: Links documents to their context (see 2.3), enabling the following:
① Appropriate access and application of authorization rules for business applications and related documents
② Enforcement of appropriate disposal rules
③ Migration of documents related to specific business functions or activities to new environments during organizational restructuring
The business classification scheme is preferably based on business functions and activities rather than organizational structure to maintain flexibility in response to organizational changes.
(2) Confidentiality Classification: Documents are marked according to their confidentiality level (e.g., Top Secret, Internal Confidential) using appropriate markings (e.g., classified markings), and handling controls are applied based on this classification.
6.4 Access Authority Management
Access authority management is executed to control the level of access authority for files and folders (e.g., read-only or edits enabled) for each accessing party (individual or group).
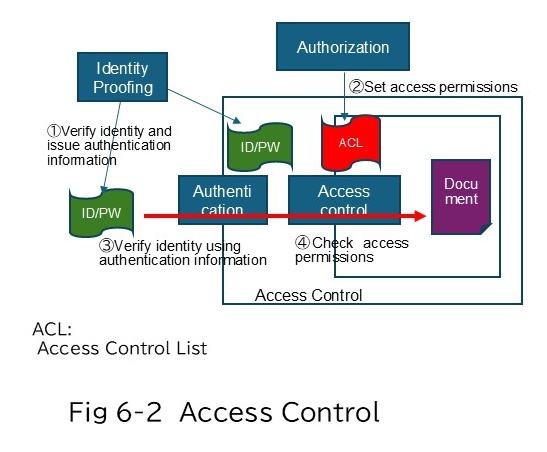
As the basic rule, access authorization must be granted for the appropriate scope of authority of the operating party. However, attention must also be paid to statutory and contractual provisions. (Figure 6-1)
In addition, the access authorization level requires regular review in response to changes in the statutory regulation environment and in business activities, including personnel replacement, and should be updated and monitored on a daily basis.
6.5 Metadata
Metadata may be called properties or attributes. For document and information management to be executed appropriately, each document is linked with metadata, such as a title, category, keywords, creator, data creation date, preservation expiry date, location of the original data, etc. Metadata is embedded in the document and is managed independent of the document for use in search and preservation period management. Normally, basic metadata for document and information management is generated in the document creation phase. More information is added when needed in the following phases of processing, preservation and disposition.
7. Implementation of Document and Information Management
7.1 Coordination with the Management System
The management system refers to the scheme in which the policies and objectives are established and instructions and control are executed in the organization appropriately in order to achieve the objectives.
The management of document, such as regulations, manuals and business results, is fundamental to a wide variety of the management systems represented by ISO 9000, ISO 14000 and ISO 27000 as mentioned in 5.2.
Because document and information management satisfies the requirements of "documented information" for these management systems, its execution serves as the core of document and information management for these systems.
7.2 Risk Management
7.2.1 Risks requiring attention in document and information management
Risk management refers to the activities aimed at searching for latent risks and examining into and deciding what should be done, such as considering and putting into place methods to avert such risks and minimize damages. Document and information management must take the following risks into account as business risks.
The risks require regular review, taking into consideration changes in the environment.
- Information security risks
- Compliance risks
- Disaster risks
- Reputation risks
Note: In contrast to risk management, crisis control refers to the responses to an incident or accident that has already taken place.
Since electronic document exists on an IT platform and is exchanged via networking, action on information security risks is essential.
Risks related to information assets are classified largely into physical, technological and human threats, as shown in Table 7-1.
Table 7-1 Examples of Threats
| Threat | Examples |
|---|---|
| Physical Threats | Break-in, destruction, failure, power failure, natural disaster, etc. |
| Technological Threats | Unauthorized access, eavesdropping, malware, tampering or deletion, DoS attack, identity theft, etc. |
| Human Threats | Erroneous operation, removal from premises, misconduct, inappropriate password management, etc. |
Examples of compliance risks, on the other hand, are the inappropriate handling or leakage of personal information, loss or damage of statutory preservation documents and the violation of rights. Natural disaster risks include force majeure events such as earthquakes and typhoons and cannot be excluded from consideration. Reputation risks related to corporate business activities must also be taken into account.
7.2.2 Risk prevention measures
To address physical and technological threats, such as loss of document, etc., measures such as data backup are implemented to avert such risks. Other risks are handled with attention to their respective levels of gravity and the potential costs incurred, with the execution of appropriate measures, including risk acceptance. If a risk cannot be ignored and cannot be addressed with any countermeasure, there is the need for changes in the underlying system.
Table 7-2 shows the threats to electronic documents and examples of preventive measures.
Table 7-2 Threats to Electronic Documents and Examples of Preventive Measures
| Threat | Preventive Measures |
|---|---|
| Theft or Leakage | Encryption; access control; version/history management |
| Tampering, Alteration or Substitution | Electronic signature and time stamp; version/history management |
| Disclaimer | Electronic signature |
| Time and Date Disclaimer | Time stamp |
| Identity Theft | Electronic signature |
| Deletion or Loss | Document management; version/history management |
| Loss | Search function |
| Loss of Readability | Standardization of viewer and data format, etc. |
| Loss of Provability | Extended processing with an advanced electronic signature or secure preservation system (including version/history management), etc. |
For protection against malware, attention must be paid to the application of program updates as swiftly as possible and when the software program update is distributed.
Since anti-malware software cannot detect all of the threats, caution must be exercised so as not to open files of unknown origin.
Information Security Incidents
An information security incident is an accident or incident that threatens information security and likely to affect business operations. As part of crisis control, documentation for emergency procedures should be made in advance, in order to enable an instantaneous emergency response.
Similarly, natural disasters must be addressed in terms of the protection of vital records as part of the business continuity plan, along with documentation of the emergency procedures in order to enable a swift response, depending on the circumstances.
END
